
Benefits of Monitoring the Dark Web
Introduction
What people see on search engines, like Google,…
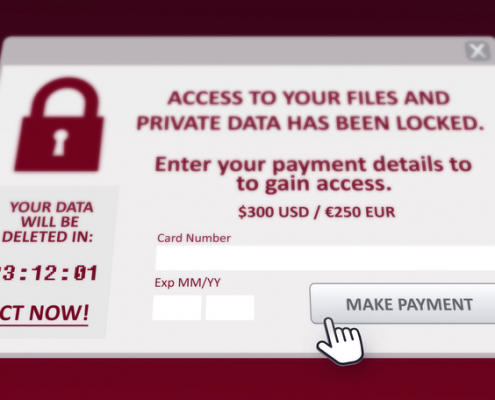
Ransomware's Profit Centers
Ransomware has evolved. Criminals are no longer satisfied with only encrypting your data and asking for money. Find out what the cyber-thieves are up to now.

Deception NEVER Takes A Vacation
Your phone is a target! Thieves create real-looking fake apps and post them in authentic app stores. Do your research before downloading an app.

Security In A Connected World
Wi-Fi and Smart Devices go together. To stay safe, you need to take precautions. Read this post and learn how to take control of your security in an always-connected world.

Your Phone—Always Connected—Always At Risk
Do you use your cell phone to make purchases? Next time, think again. Read Carlos's story to see why.

31 Tips To Keep You Safe
Cybersecurity Awareness Month may be over, but these 31 tips are timeless. Include them into your daily practices. Be safe.

Is Social Engineering Effective?
Social Engineering is the method of choice for hackers. Uber or Rockstar Games learned this the hard way. Learn from these breaches to recognize and prevent being victimized.

A Horror: Cyber Crime!
Scary movies are a staple this time of year. But you can learn from the actor’s “mistakes” and keep yourself safe from cybercrime. Read how.

The Recipe for Strong Cybersecurity
Getting protected is like following a good recipe. Use the proper ingredients in the correct order, and you will be more protected than most.

Doctor Visits
The Dark Web is a scary place but ignore it at your peril. All businesses need a program that protects their network and monitors the Dark Web for breaches.
