How To Identify A Phishing Email—An Example
One of our good clients sent us a phishing email supposedly from Microsoft. It fooled a very experienced user and so would be a good example to use to show our readers how to identify Phishing emails.
Fortunately, the bogus link did not forward to an infected website where ransomware could have been instantaneously downloaded, completely compromising the user’s PC and the entire company network. In this case, the links went to a bogus site asking for Microsoft 365 login credentials.
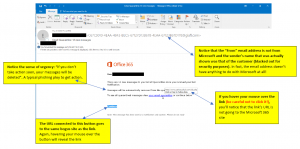
Here is the actual email with annotations of what to look for:
On the surface, the email appears real—after all, it has the Office 365 logo! That’s exactly what hackers want you to think. Many people look no further than the logo before they act. But look very closely:
- The “From” email address is not Microsoft’s. Why would Microsoft be contacting you from a strange domain?
- If you hover your mouse over the link in the message and/or the “Continue” button, you’ll see the URL they go to is not Microsoft’s site. Again, why would Microsoft send you to a strange site?
- Just for added kicks, the hacker through in the always present “sense of urgency” trying to get users to take an action without thinking it through.
Most phishing emails follow the concepts noted above. Look closely at all unsolicited emails BEFORE you start clicking links or opening attachments. It will save you and your company a lot of grief.
Now that you know how to identify bogus emails, it would be wise to pass this information on to all your employees so they know what to look for.
For a list of immediate steps to take to protect yourself and your company read our recent post, Hackers Step Up Phishing Attacks in our Letter X Blog.
XSolutions is an Elite Partner of Datto, the world leader in Hybrid-Cloud Business Continuity solutions whose systems protect 250+ Petabytes of data with over 800 employees around the globe. Call (845) 362-9675 and let us introduce you to the ultimate defense against data loss—whatever the cause.