Posts
 https://xsolutions.com/wp-content/uploads/2020/09/DRP-Dial-Grid-Xlarge-scaled.jpg
1258
2560
Joe Imperato, Sr.
https://xsolutions.com/wp-content/uploads/2023/09/XSol-Logo-header-300x138.png
Joe Imperato, Sr.2022-03-30 07:15:002022-03-31 15:05:03How The Right Solution Can Save Your Business
https://xsolutions.com/wp-content/uploads/2020/09/DRP-Dial-Grid-Xlarge-scaled.jpg
1258
2560
Joe Imperato, Sr.
https://xsolutions.com/wp-content/uploads/2023/09/XSol-Logo-header-300x138.png
Joe Imperato, Sr.2022-03-30 07:15:002022-03-31 15:05:03How The Right Solution Can Save Your Business
10 Lessons From The Past
Those who ignore history are doomed to repeat it. Here’s 10 security lessons we should learn from the past.

Business Backups: The Rule Of 3
Businesses should back up their data and keep multiple copies for redundancy. Find out what the rule of 3 is and how it can help your business.

Case study: Culligan Water
Culligan needed to update their computer systems and software and bring the company into the 21st century in order to compete in today's environment. XSolutions was there to help.

Case study: Global Containers
To reliably connect their staff located globally, with their data and inventory, Global Containers needed a strong cloud solution. See the results.

What You Should Know About Intelligent Business Continuity Versus Traditional Backup
Data backup alone does not guarantee a quick recovery, only a Business Continuity solution can. Read and find out why.

Is a System Image the Same as a Backup?
Data only backup systems have their place for very small firms. Larger companies need to consider image-based backup solutions.
Is RAID A Backup Strategy?
RAID and backups are two very distinct technologies. One should not be used as a substitute for the other. In fact, you need both. Read on to find out why.
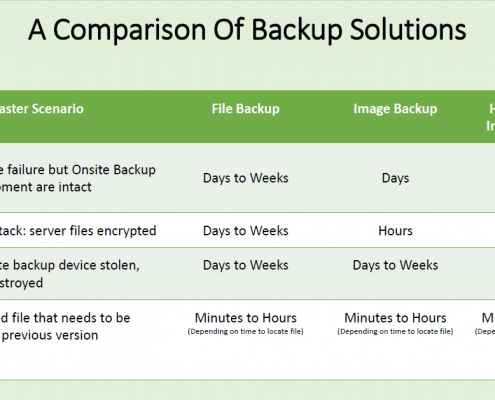
Why Businesses Pay The Ransom
The reason many businesses are forced to pay the ransom is poor planning. Know the different types of backups to save your company.

Which Is Better: Full, Incremental, or Differential Backups?
Selecting a Business Continuity Disaster Recovery solution is serious business. Select the wrong one, and you could go out of business.
