What You Should Know About Business Email Compromise
Introduction
CEO-Wire Fraud, commonly known as Business Email Compromise (BECs), is a dangerous Social Engineering attack that costs businesses billions in losses. It has plagued large companies and decimated smaller businesses for many years.
The typical Modus Operandi of BEC fraudsters:
- Hackers often stalk target companies on the internet (i.e., Google, social media, specialized commercial databases) for weeks and even months to find people within a company with the proper authority to wire funds without additional oversights.
- Through spear-phishing, hackers attempt to get their targets to click on infected links or open contaminated attachments, exposing their corporate credentials.
- Once in the network, the fraudsters gain access to the victim’s account and study the emails passing to and from the employee and the company’s CEO/management.
- They’ll spoof legitimate email addresses using a variety of means.
- Hackers then send emails to their target, usually requesting money to be paid to fictitious vendors while re-directing responses to a bogus account they control.
By studying the company’s communications, hackers learn when the CEO is not in the office, the financial institutions the target company deals with, etc. This information is used to make their bogus communications seem real and believable.
Wired funds go primarily to banks outside of the country or are withdrawn immediately and sent to a foreign bank, diminishing any chance of recovery after the fraud is detected.
Anatomy Of A Real BEC Attack
Note: I redacted identifying information in the emails to protect privacy.
Email #1:
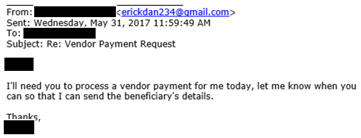
Comment: The attacker contacts his target, masquerading as the boss.
Here’s a crucial piece of evidence: The “From” address had the boss’s name, but the sender’s email was not from a company email address and didn’t even contain the boss’s name. Instead, it was a Gmail account—a dead giveaway. Most people do not realize this and only look at the boss’s name before acting.
Email #2:
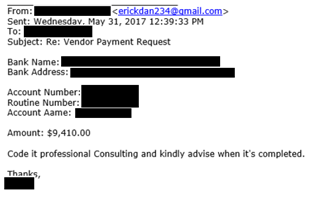
Comment: The attacker sends detailed instructions to the target for the wire transfer. Notice that the amount is below $10,000. Small amounts usually don’t trigger additional management approval, depending on the target company’s size.
Email #3:
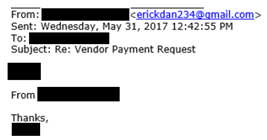
Comment: Here’s a critical point. This attacker knew that the targeted company had an account at a particular bank (which we redacted). As mentioned, scammers do their homework. Naming a bank or other “insider information” is intended to give their target confidence that the person sending the email is indeed the boss.
Email #4:

Comment: A glitch! Company procedures require the boss’s direct approval to wire funds even for small amounts. When the employee informs the attacker, the scammer comes up with a story.
Email #5:
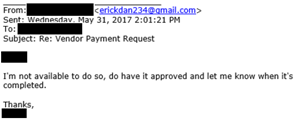
Comment: The attacker tries to salvage the scheme by explaining that he cannot approve it and tries to rely on his position as the “boss” to intimidate the employee into acting without the required approval.
Email #6:

Comment: Things aren’t going so well at this point. Company procedures call for the boss’s direct approval, which the scammer cannot do without risking detection.
Email #7:
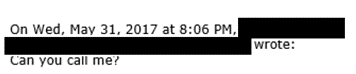
Comment: Suspicious, the employee now asks to talk to the boss directly. The attacker knows that once this happens, the ploy is over. So, he makes up another excuse.
Email #8:
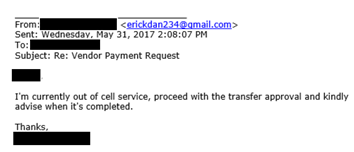
Comment: The attacker gives what seems like a reasonable explanation of why he cannot speak directly with his employee and again tries to manipulate the target into finding a way to wire the funds.
Email #9:
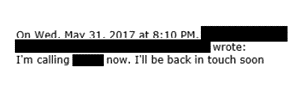
Comment: The employee calls the bank (redacted) and then directly phones the boss, verifying that he never made the wire request. The attack fails.
Key Points To Remember:
- Social Engineers are one of the most feared types of attackers. They know human nature and how to tap into emotions to get the desired response.
- When committing CEO-Wire Fraud, scammers go to great lengths to research their prey. The more they know about their target, the better they can pass themselves off as an “insider.”
- To guard against BEC, procedures should be in place to require additional approvals when wiring funds, even small amounts.
- Train employees on the type of information they can divulge to the public versus specific information they should never disclose to anyone. One of a good Social Engineer’s skills is putting together a detailed profile of a target company using various bits of seemingly unimportant information gleaned through the internet and telephone conversations.
- Train employees on how to spot bogus emails. In the instance above, why would the boss be using a non-company email account?
- Secure all home computers used to log into the corporate network, especially since the pandemic. Infected home computers can pass malware to corporate networks when accessing company systems.
- Employees should know that it is OK to question instructions when asked to bypass procedures no matter who makes the request. Social Engineers use human nature against their targets, and they know it is uncomfortable for most employees to question authority.
Use Technology In Addition To Employee Training
Every business, regardless of size, should have safeguards built within its network.
SPAM filters are essential to reduce bogus emails, but Artificial-intelligent (AI)-driven email security is better and very affordable.
Every company should have a Backup Disaster Recovery (BDR) system to ensure that all data is quickly recoverable to maintain operations.
If you don’t have an in-house IT Department, then get a qualified Managed Services Provider (MSP) with advanced security capabilities on board ASAP.
XSolutions is an Elite Partner of Datto, the world leader in Hybrid-Cloud Business Continuity solutions. We provide Disaster Recovery as a Service (DRaaS), Backup as a Service (BaaS), Cloud Data Protection (CDP), and Managed IT Services (MSP). Call (845) 362-9675 for a free consultation. Backup & Disaster Recovery| Cloud Data Protection |Managed IT Services





