Anatomy Of A CEO-Wire Fraud Attack
CEO-Wire Fraud is a dangerous Social Engineering attack that cost businesses billions in losses. A good Social Engineer will study potential victims sometimes for months before attacking and craft convincing spoofed emails, targeting accounting personnel with wire transfer responsibilities.
Recently, one of our best clients experienced such an attack and they graciously allowed us to use the email stream as an educational tool. This attack ultimately failed, but schemes like this succeed every day, so it is important that you train your staff accordingly. I’m not including all of the emails since there were over 15 of them, but I’ll show you enough so you’ll get the idea of how this type of attack unfolds.
Note: I redacted identifying information in the emails to protect our client’s privacy.
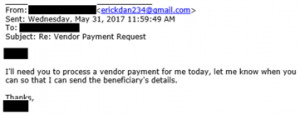
Email #1:
Comment: The attacker contacts his target masquerading as the boss. Hackers do their homework, often stalking companies on the internet (i.e. Google, social media, specialized commercial databases and using social engineering tactics) for weeks and even months to find people within a company with the right responsibilities to target.
Here’s a crucial piece of evidence: The “From” address had the boss’s name but the email of the sender was not from a company email address and in act didn’t even contain the boss’s name. Instead it was a Gmail account—a dead giveaway. Most people do not realize this and only look at the boss’s name before acting.
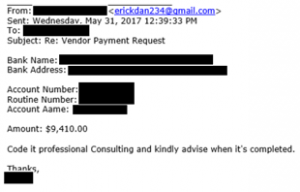
Email #2:
Comment: The attacker sends the target detailed instructions for the wire transfer. Notice that the amount is below $10,000. This is probably due to the attacker’s belief that a small amount would not arouse suspicion, be considered routine and not trigger additional approvals.
Email #3:
Comment: Here’s a key point. This attacker knew that the targeted company had an account at a particular bank (which we redacted). As mentioned, scammers do their homework. Naming a bank or some other “insider information” is intended to give their targets confidence that the person sending the email is indeed the boss.
Email #4:
Comment: A glitch! Company procedures require the boss’s direct approval to wire funds. When the employee informs the attacker, the scammer comes up with a story.
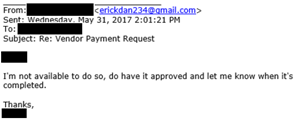
Email #5:
Comment: The attacker tries to salvage the scheme by explaining that he cannot approve it and tries to rely on his position as the “boss” to intimidate the employee into acting without the required approval.
Email #6:
Comment: Things aren’t going so well at this point. Company procedures call for the boss’s direct approval, which the scammer cannot do without risking detection.
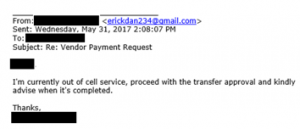
Email #7:
Comment: Suspicious, the employee now asks to talk to the boss directly. The attacker knows that once this happens, the ruse is over. So, he makes up another excuse.
Email #8:
Comment: The attacker gives what seems like a reasonable explanation of why he cannot speak directly with his employee and again tries to manipulate the target into finding a way to wire the funds.
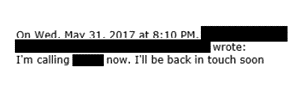
Email #9:
Comment: The employee calls the bank (redacted) directly and then calls the boss, who verifies that he never made the wire request. The attack fails.
Key points:
- Social Engineers are one of the most feared type of attackers. They know human nature and how to tap into emotions to get a desired response. A Social Engineer with good programming skills is an absolute nightmare to businesses and law enforcement.
- When committing CEO-Wire Fraud, scammers go to great lengths to research their prey. The more they know about their target, the better they can pass themselves off as an “insider”.
- To guard against a CEO-Wire Fraud attack, procedures should be in place to positively identify those with authority to approve such transactions.
- Employees must be trained on the type of information they can divulge to the public versus specific information they should never divulge to anyone. One of the skills of a good Social Engineer is the ability to put together a detailed profile of a target company using various bits of seemingly unimportant information gleamed through the internet and telephone conversations.
- Employees should be trained on how to spot bogus emails. In the instance above, why would the boss be using a non-company email account?
- Home computers used to log into the corporate network should be secured. Hackers may send phish emails to employees’ home PCs knowing that many are not patched, are running outdated/vulnerable software and using less effective free anti-virus (AV) products or having no AV at all. Once infected, scammers can penetrate corporate networks when the employee logs in from home.
- Employees should be encouraged to question suspicious instructions especially when asked to bypass procedures no matter who is making the request and to immediately notify their supervisor. Social Engineers use human nature against their targets and the fact that most are uncomfortable questioning authority.
Sound operational procedures, employee training, the willingness to question instructions when things don’t seem right without fear of retribution, a managed and maintained corporate network and a comprehensive Backup/Disaster Recovery solution will go a long way to keeping your business safe.
Don’t be a victim. Review your company’s operational procedures as they relate to wiring funds, setting up vendors in the accounting system and appropriate approval levels. The sad fact is that many times this type of fraud succeeds resulting in large financial losses. Be proactive and take the proper steps now.
XSolutions is an Elite Partner of Datto, the world leader in Hybrid-Cloud Business Continuity solutions whose systems protect 250+ Petabytes of data with over 800 employees around the globe. Call (845) 362-9675 and let us introduce you to the ultimate defense against data loss—whatever the cause.